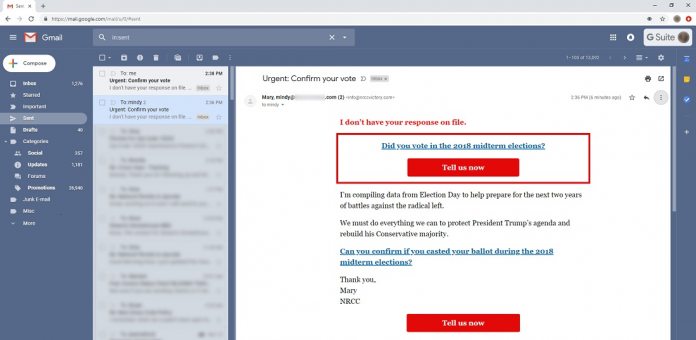
Because of the vulnerability, phishing campaigns and scammers could have an easy access to trick unsuspecting users into clicking a link. For example, a user might open the placed email to see what it is and click a link within. The flaw was discovered and reported by software developer Tim Cotton. He says the vulnerability comes from how Gmail organizes folders. Google’s system denotes sent emails based on the from field in the address. In other words, an attacker could specifically compose an email have the target email address in the from field. If this happens, the email will be instantly moved to the persons inbox and sent folder simultaneously. “So, it appears that by structuring the from field to contain the recipient’s address along with other text, the Gmail app reads the from field for filtering/inbox organization purposes and sorts the email as though it were sent from [the recipient], despite it clearly also having the originating mailbox as [another address],” Cotton explains.
Easy Entry
This vulnerability could provide an easy way for spam email and phishing attacks. Not least because spam content may be stopped from going to the inbox but would still pass to the Sent folder. It could be easy to cause confusion amongst unwitting users without much experience. “The confusion being injected into the average user experience is an open door for malicious actors… Imagine, for instance, the scenario where a custom email could be crafted that mimics previous emails the sender has legitimately sent out containing various links,” said Cotten. “A person might, when wanting to remember what the links were, go back into their sent folder to find an example: disaster!” Additionally, attackers would have the added benefit of emails in the Sent folder appearing as if it has already been read. Some users would believe they are already seen the email without any issues. Cotten says he has reported the issue to Google, but so far, the company has not confirmed it officially.